How to update sudo version on Linux
Last updated on February 6, 2021 by Dan Nanni
sudo command, and I want to upgrade sudo to the latest version immediately to fix its vulnerability on my Linux system. How can I update sudo version on [insert your Linux distro]?On Linux, the sudo command (short for "substitute user do" or "superuser do") is designed to allow a user to run a program with access capabilities of another user (most commonly the superuser "root"). sudo is commonly used to give selected users administrative control on a Linux system. Although sudo has built-in mechanisms to prevent misuse (e.g., security policies, input/output logging), the potential impact of any vulnerability in sudo command is still extremely high.
For example, the latest heap buffer overflow vulnerability discovered in sudo (CVE-2021-3156) can trigger privilege escalation and allow any unprivileged user (those not in the sudoers list, or even nobody) to bypass password authentication and gain the root access. This vulnerability can easily be exploited as the second-stage attack once a low-level service account gets breached via brute-force attacks.
Since sudo is available on most Linux distributions by default, any vulnerability in sudo will most likely affect you directly.
How to Check if Your sudo Has Vulnerability (CVE-2021-3156)
Here I describe how to check if your sudo is vulnerable to the latest heap buffer overflow vulnerability (CVE-2021-3156). While the instruction is very much specific to this vulnerability, it can be easily adjusted for any other sudo vulnerabilities based on corresponding CVE vulnerability disclosures.
Method One: Check sudo Version
You can check the version of your sudo with the following command, and compare it against affected versions.
$ sudo --version
Versions of sudo affected by CVE-2021-3156:
- All legacy versions of
sudofrom 1.8.2 to 1.8.31p2 - All stable versions of
sudofrom 1.9.0 to 1.9.5p1
Method Two: Test the Vulnerability of CVE-2021-3156 from the Command Line:
From the sudo version alone, you may not tell if sudo is vulnerable or not since the patch can be backported. A more reliable method is to test the vulnerability directly. To test if your sudo is affected by the heap buffer overflow vulnerability, you can use the following command line.
First log in to your Linux system as a non-root user, and then run:
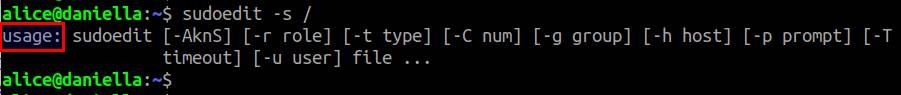
$ sudoedit -s /
If your sudo is vulnerable, it will display an error message that says "sudoedit: /: not a regular file"

If your sudo is already patched, it will show a usage message starting with usage:
Update sudo Version on Supported Linux Distros
Once you find that your sudo is affected by a known vulnerability, you should update sudo immediately. The easiest way is of course to use the default package manager of your Linux system. However, this method is only applicable if your Linux distro has not reached End-of-Life (EOL). If your Linux distro is no longer maintained because its support lifecycle has expired, the repositories will not be updated with security patches. In this case, you cannot update sudo with a package manager, and you need to update it manually, as described next.
Here I assume that your Linux system is still supported. Before updating sudo, an optional step is to check the changelog of the sudo package to confirm that the sudo package has been patched for a known vulnerability. In this example, the vulnerability under consideration is CVE-2021-3156. You can skip checking the changelog if you are upgrading sudo as part of regular maintenance.
Update sudo on Ubuntu, Debian or Linux Mint:
To check the vulnerability patch for sudo in the changelog of its DEB package:
$ sudo apt update; apt changelog sudo | grep CVE-2021-3156
- debian/patches/CVE-2021-3156-pre1.patch: check lock record size in
- debian/patches/CVE-2021-3156-pre2.patch: sanity check size when
- debian/patches/CVE-2021-3156-1.patch: reset valid_flags to
- debian/patches/CVE-2021-3156-2.patch: add sudoedit flag checks in
- debian/patches/CVE-2021-3156-3.patch: fix potential buffer overflow
- debian/patches/CVE-2021-3156-4.patch: fix the memset offset when
- debian/patches/CVE-2021-3156-5.patch: don't assume that argv is
Once you confirm that the patch is available, go ahead and update sudo with:
$ sudo apt update; sudo apt --only-upgrade install sudo
Note that, even after a successful update, sudo version may remain the same or one of affected versions. Rest assured. It is simply because often times a vulnerability patch is simply backported to an existing sudo version. Thus, to verify the patch is successfully applied, it is recommended to test sudo against the vulnerability, as described previously.
Update sudo on Fedora or CentOS:
To check the vulnerability patch for sudo in the changelog of its RPM package:
$ repoquery --changelog sudo | grep CVE-2021-3156
Fedora 33 openh264 (From Cisco) - x86_64 3.6 kB/s | 3.2 kB 00:00 Fedora Modular 33 - x86_64 952 kB/s | 1.5 MB 00:01 Fedora Modular 33 - x86_64 - Updates 1.5 MB/s | 1.5 MB 00:01 Fedora 33 - x86_64 - Updates 2.0 MB/s | 10 MB 00:05 Fedora 33 - x86_64 1.3 MB/s | 15 MB 00:10 RPM Fusion for Fedora 33 - Free - Updates 1.1 MB/s | 414 kB 00:00 RPM Fusion for Fedora 33 - Free 1.3 MB/s | 964 kB 00:00 - fixed CVE-2021-3156 sudo: Heap buffer overflow in argument parsing
Once you confirm that the patch exists, go ahead and update sudo with:
$ sudo dnf update sudo
Note that, even after a successful update, sudo version may remain the same or one of affected versions. Rest assured. It is because often times a vulnerability patch is simply backported to an existing sudo version. To double check on that, it is always a good idea to re-test sudo against the vulnerability, as described previously.
If your CentOS or Fedora system has reached EOL, you will need to manually update sudo as described next.
Update sudo Version on Unsupported Linux Distros
If you are running an old Linux distribution which has reached EOL and is not supported (e.g., CentOS 6, Ubuntu 17.04), unfortunately you are on your own in regards to applying security patches. For some Linux distros, at least you can download the latest stable version of sudo binary package from the official website. For example, they provide an RPM package of the latest sudo for unsupported RHEL/CentOS 5 and 6.
If a pre-built binary package is not available, you can build the latest stable version (1.9.5p2 as of now) of sudo from the source, and manually install it. You can also consider using CheckInstall to build a DEB/RPM package from the source.
The following describes how to manually build and install sudo from the source.
For Ubuntu, Debian or Linux Mint:
$ sudo apt install make gcc $ wget https://www.sudo.ws/dist/sudo-1.9.5p2.tar.gz $ tar -xf sudo-1.9.5p2.tar.gz $ cd sudo-1.9.5p2 $ ./configure --prefix=/usr $ make $ sudo make install
For CentOS or Fedora:
$ sudo dnf install make gcc $ wget https://www.sudo.ws/dist/sudo-1.9.5p2.tar.gz $ tar -xf sudo-1.9.5p2.tar.gz $ cd sudo-1.9.5p2 $ ./configure --prefix=/usr $ make $ sudo make install
After installation, verify that sudo is up-to-date:
$ sudo --version
Sudo version 1.9.5p2 Sudoers policy plugin version 1.9.5p2 Sudoers file grammar version 48 Sudoers I/O plugin version 1.9.5p2 Sudoers audit plugin version 1.9.5p2
Support Xmodulo
This website is made possible by minimal ads and your gracious donation via PayPal or credit card
Please note that this article is published by Xmodulo.com under a Creative Commons Attribution-ShareAlike 3.0 Unported License. If you would like to use the whole or any part of this article, you need to cite this web page at Xmodulo.com as the original source.
Xmodulo © 2021 ‒ About ‒ Write for Us ‒ Feed ‒ Powered by DigitalOcean

