How to monitor DHCP traffic from the command line on Linux
Last updated on September 21, 2020 by Dan Nanni
If you want to monitor DHCP communication between a DHCP server and a client, you can run a packet sniffing tool on the same local network, and capture DHCP traffic. There are a couple of sniffing tools you can use.
Method One: tcpdump
The first method to capture DHCP traffic is to use venerable tcpdump tool. In this case, you want to define a filter so that tcpdump dumps only DHCP related traffic. In DHCP, UDP port 67 is used by a DHCP server, and UDP port number 68 is used by DHCP clients. Thus, you want to capture traffic with port number 67 or 68 as follows.
$ sudo tcpdump -i <network-interface> port 67 or port 68 -e -n
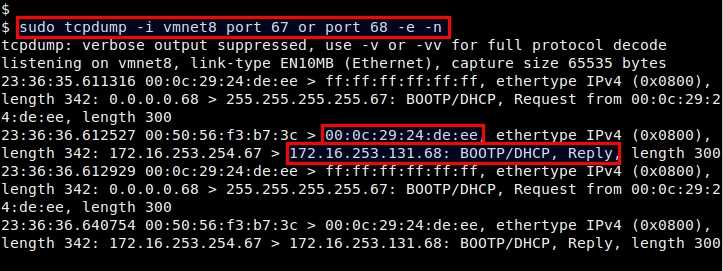
The above tcpdump output shows that IP address 172.16.253.131 is assigned to a client with hardware address 00:0c:29:24:de:ee.
Method Two: dhcpdump
The second method to monitor DHCP requests and responses is to use dhcpdump, which is a command-line DHCP packet dumper program.
To install dhcpdump on Debian or Ubuntu:
$ sudo apt-get install dhcpdump
To install dhcpdump on CentOS, first set up Repoforge on your system, and then run:
$ sudo yum install dhcpdump
To install dhcpdump on Fedora:
$ sudo yum install dhcpdump
The following command will dump DHCP requests and responses in a human-readable format.
$ sudo dhcpdump -i <network-interface>
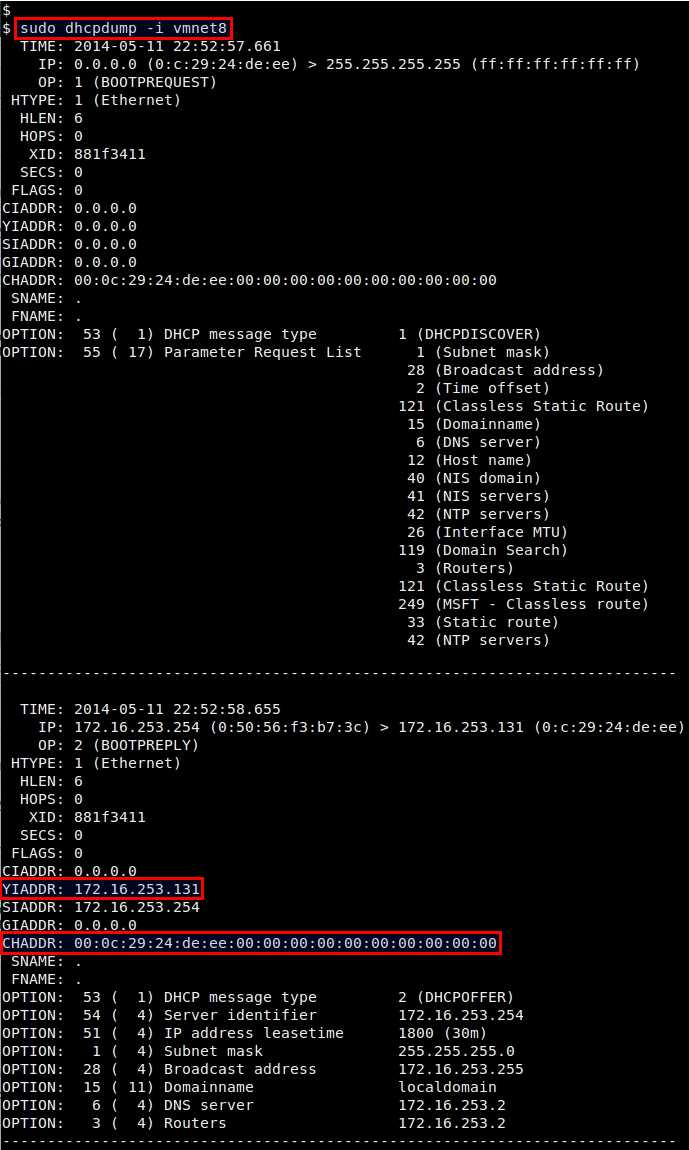
The output shown by dhcpdump is more detailed than that of tcpdump. YIADDR field is populated with the IP address offered by a DHCP server to a client, and CHADDR field is the hardware address of the requesting client. It also shows other information such as DHCP lease time, subnet mask, DNS server, etc.
dhcpdump can filter DHCP responses such that it captures only DHCP responses sent to a particular hardware address.
For example, the following command will capture DHCP response packets sent to client whose hardware address starts with 00:c1:b5.
$ sudo dhcpdump -i eth0 -h ^00:c1:b5
Support Xmodulo
This website is made possible by minimal ads and your gracious donation via PayPal or credit card
Please note that this article is published by Xmodulo.com under a Creative Commons Attribution-ShareAlike 3.0 Unported License. If you would like to use the whole or any part of this article, you need to cite this web page at Xmodulo.com as the original source.
Xmodulo © 2021 ‒ About ‒ Write for Us ‒ Feed ‒ Powered by DigitalOcean

